Cybersecurity threats are lurking where you least expect them—within our critical infrastructure.
From power grids to water treatment facilities, these vital systems are under constant digital attack. As our society becomes more interconnected, the stakes are higher than ever.
Understanding these threats goes beyond the tech world; it impacts everyone who relies on these essential services. Cybercriminals exploit vulnerabilities, targeting systems that we often take for granted.
This article explores the types of attacks affecting critical infrastructure and the challenges faced by those tasked with protecting it.
The insights might change how you perceive cybersecurity and its implications for our daily lives.
Key Takeaways
- Critical infrastructure encompasses essential sectors like energy, transportation, telecommunications, water, and healthcare systems.
- Common cybersecurity threats include malware, phishing, DDoS attacks, APTs, and insider threats.
- Industrial Control Systems often lack robust security features and are vulnerable to attacks.
- Successful attacks can cause widespread disruptions, economic losses, and compromise national security.
- Mitigation strategies involve access controls, patch management, security assessments, encryption, and employee training.
Types of Critical Infrastructure

While many people think of significant infrastructure as just power grids and water systems, it actually encompasses a much broader range of indispensable services and facilities.
You’ll find that significant infrastructure includes sectors essential to a nation’s security, economy, and public health.
The energy sector is a primary component, covering electricity generation, oil, and natural gas systems.
Transportation networks, including roads, railways, airports, and seaports, are equally important.
Telecommunications and information technology systems form the backbone of modern communication and data exchange.
Water and wastewater management systems guarantee access to clean water and proper sanitation.
Healthcare and public health facilities are fundamental for maintaining population well-being.
Financial services, including banking and stock exchanges, are significant for economic stability.
You’ll also find that emergency services, such as police, fire departments, and disaster response teams, are part of this infrastructure.
Government facilities, chemical plants, food and agriculture systems, and dams are additional significant sectors.
Understanding the diverse nature of significant infrastructure is key to appreciating the complexity of cybersecurity challenges these sectors face.
Common Cybersecurity Threats

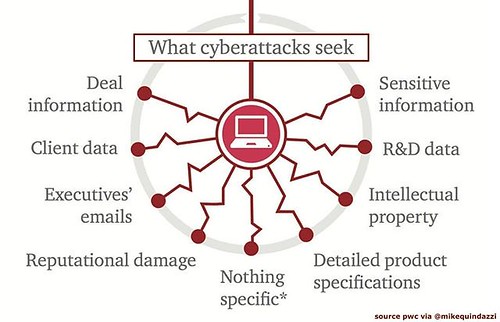
Facing an ever-evolving landscape of digital dangers, critical infrastructure sectors are prime targets for various cybersecurity threats. These threats can cause widespread disruption, financial losses, and even physical harm.
You’ll find that malware, including viruses, worms, and ransomware, tops the list of common threats. Attackers use these malicious programs to infiltrate systems, steal data, or encrypt files for ransom.
Phishing attacks are another prevalent threat, where cybercriminals trick employees into revealing sensitive information or granting access to secure systems.
Distributed Denial of Service (DDoS) attacks can overwhelm networks, rendering critical services unavailable. Advanced Persistent Threats (APTs) involve sophisticated, long-term campaigns targeting specific organizations or sectors.
Supply chain attacks exploit vulnerabilities in third-party vendors or software, compromising entire networks. Insider threats, whether intentional or accidental, pose significant risks as employees have direct access to sensitive systems.
Zero-day exploits target unknown vulnerabilities before patches are available. Social engineering tactics manipulate human psychology to bypass security measures.
As technology advances, you’ll also need to watch for emerging threats like AI-powered attacks and quantum computing risks.
Vulnerabilities in Industrial Control Systems

Industrial Control Systems (ICS) form the backbone of critical infrastructure, yet they harbor numerous vulnerabilities that make them attractive targets for cybercriminals.
You’ll find that many ICS components were designed decades ago, prioritizing functionality over security. This legacy architecture often lacks basic cybersecurity features like encryption or authentication.
You should be aware that ICS networks are frequently connected to corporate IT networks, creating potential entry points for attackers. Outdated software and firmware, coupled with infrequent patching, exacerbate these vulnerabilities. Many systems still use default passwords or have weak access controls, making unauthorized access easier.
You’ll notice that ICS protocols, such as Modbus and DNP3, weren’t built with security in mind. They lack encryption and integrity checks, leaving them susceptible to man-in-the-middle attacks and data manipulation.
Remote access capabilities, while convenient for maintenance, can be exploited if not properly secured.
You must understand that the increasing adoption of Internet of Things (IoT) devices in industrial settings introduces new attack vectors. These devices often have limited security features and can serve as entry points into the broader ICS network.
Impact of Successful Attacks

When cybercriminals successfully exploit vulnerabilities in critical infrastructure, the consequences can be devastating. You’ll see disruptions to essential services that can affect millions of people. Power outages may leave entire cities in darkness, while water treatment plant attacks could compromise the safety of drinking water.
Transportation systems might grind to a halt, causing chaos and economic losses. Successful attacks on financial institutions can lead to widespread data breaches, identity theft, and financial instability.
Healthcare systems are particularly vulnerable, with cybercriminals potentially gaining access to sensitive patient data or disrupting life-saving medical equipment. In the energy sector, attacks could cause fuel shortages, price spikes, and environmental disasters.
The impact isn’t limited to immediate service disruptions. You’ll notice long-term effects on public trust, national security, and economic stability. Recovery from these attacks can take months or even years, costing billions in damages and lost productivity.
Additionally, successful attacks embolden cybercriminals, potentially leading to more frequent and sophisticated attempts. As our reliance on interconnected systems grows, the potential impact of these attacks becomes increasingly severe, highlighting the critical need for robust cybersecurity measures.
Mitigation Strategies and Best Practices
Three key mitigation strategies can greatly reduce the risk of cyberattacks on critical infrastructure.
First, implement robust access controls and authentication measures. You’ll need to enforce strong password policies, use multi-factor authentication, and regularly update user permissions. This limits unauthorized access and prevents potential breaches.
Second, maintain a rigorous patch management system. You must promptly apply security updates and patches to all software and hardware components. This addresses known vulnerabilities and protects against emerging threats.
Third, conduct regular security assessments and penetration testing. You should identify weaknesses in your systems before attackers do, allowing you to proactively strengthen your defenses.
Additionally, you’ll want to implement network segmentation, isolating critical systems from less secure areas.
Encrypt sensitive data both in transit and at rest to protect it from interception or theft.
Develop and regularly test incident response plans to guarantee quick and effective action during a cyberattack.
Finally, prioritize employee training on cybersecurity best practices, as human error remains a considerable vulnerability.
Conclusion
You’ve explored the complex landscape of cybersecurity threats to critical infrastructure. You’ve seen the various types of infrastructure at risk, common threats they face, and vulnerabilities in industrial control systems. You’ve learned about the potential impacts of successful attacks and discovered key mitigation strategies. Now it’s up to you to apply this knowledge, stay vigilant, and work towards strengthening the security of these essential systems. Remember, protecting critical infrastructure is everyone’s responsibility.

